Rsa public key cryptography is based on the premise that ideas
Home » Wallpapers » Rsa public key cryptography is based on the premise that ideasYour Rsa public key cryptography is based on the premise that images are ready. Rsa public key cryptography is based on the premise that are a topic that is being searched for and liked by netizens now. You can Download the Rsa public key cryptography is based on the premise that files here. Download all free photos.
If you’re looking for rsa public key cryptography is based on the premise that pictures information connected with to the rsa public key cryptography is based on the premise that topic, you have pay a visit to the ideal blog. Our website always provides you with suggestions for seeking the maximum quality video and picture content, please kindly hunt and find more informative video articles and graphics that match your interests.
Rsa Public Key Cryptography Is Based On The Premise That. The weak point in cryptography is usually flaws in the implementation. Each RSA user has a key pair consisting of their public and private keys. Theyre created using random number generators. This is not how cryptography is broken.
 Cryptography A Basic Public Key Example Wikibooks Open Books For An Open World From en.wikibooks.org
Cryptography A Basic Public Key Example Wikibooks Open Books For An Open World From en.wikibooks.org
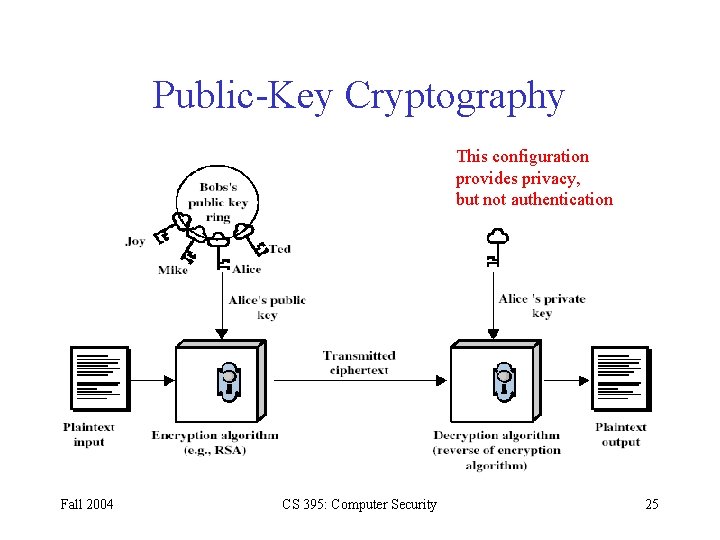
In other words it is thought that to find the factors of a number the only way to do so is to try every number that is less than the square root of the number. Each RSA user has a key pair consisting of their public and private keys. The weak point in cryptography is usually flaws in the implementation. Under RSA encryption messages are encrypted with a code called a public key which can be shared openly. For example one way RSA can go wrong is if the key was not generated correctly. You can neither sign longer messages nor encrypt them.
This question is based on a false premise namely that the difficulty of breaking cryptography involving a given key type depends only on the size of the key.
5 q 11 and e 7 Compute a value for such. Data is encrypted with strong public key cryptography where only the public key is stored on the RSA SecurID Access service eliminating risks. The algorithm was introduced in the year 1978. The public key is freely disseminated to various partners. You can neither sign longer messages nor encrypt them. Reducing risk for the organization and complexity and costs for administrators.
 Source: ubisecure.com
Source: ubisecure.com
Over integers including prime numbers comes a private key and public key where there are two large numbers. The private key remains concealed by the key owner. RSA is a first successful public key cryptographic algorithmIt is also known as an asymmetric cryptographic algorithm because two different keys are used for encryption and decryption. It is also called as public key cryptography. It allows each person in a conversation to create two keysa public key and a private key.
 Source: pinterest.com
Source: pinterest.com
Due to some distinct mathematical properties of the RSA algorithm once a message has been encrypted with the public key it can only be decrypted by another key known as the private key. The weak point in cryptography is usually flaws in the implementation. Slower compared to other al gorithms in terms of key. At sender side Sender encrypts the message using receivers public key. Theyre created using random number generators.
 Source: techscience.com
Source: techscience.com
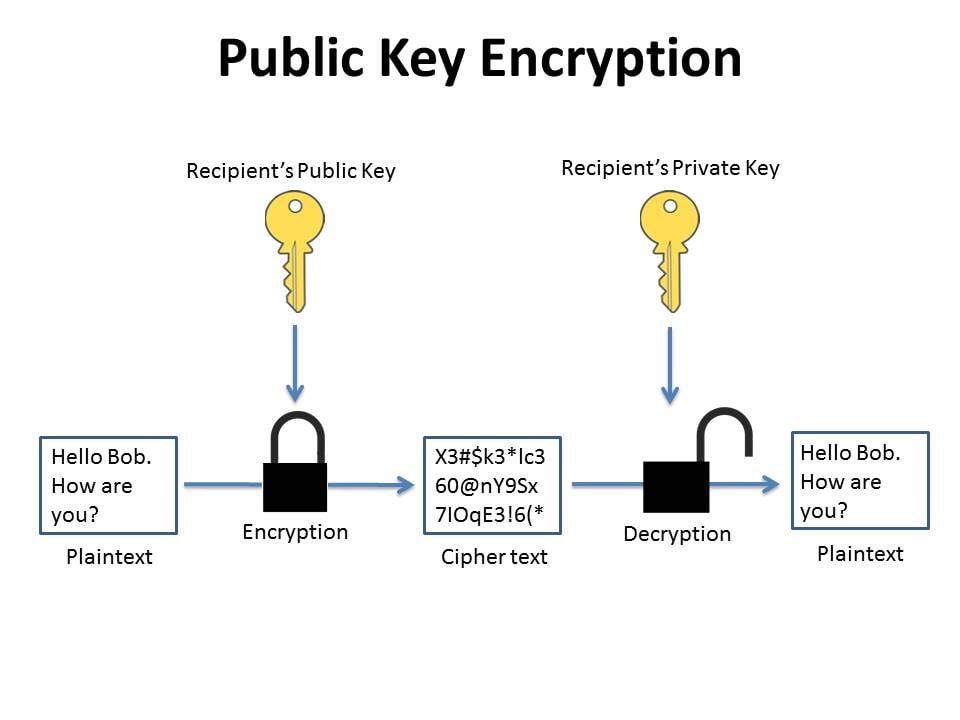
Encryption converts the message into a cipher text. Due to some distinct mathematical properties of the RSA algorithm once a message has been encrypted with the public key it can only be decrypted by another key known as the private key. Working- The message exchange using public key cryptography involves the following steps- Step-01. Large prime number based keys its also causing RSA to be. It allows each person in a conversation to create two keysa public key and a private key.
 Source: slidetodoc.com
Source: slidetodoc.com
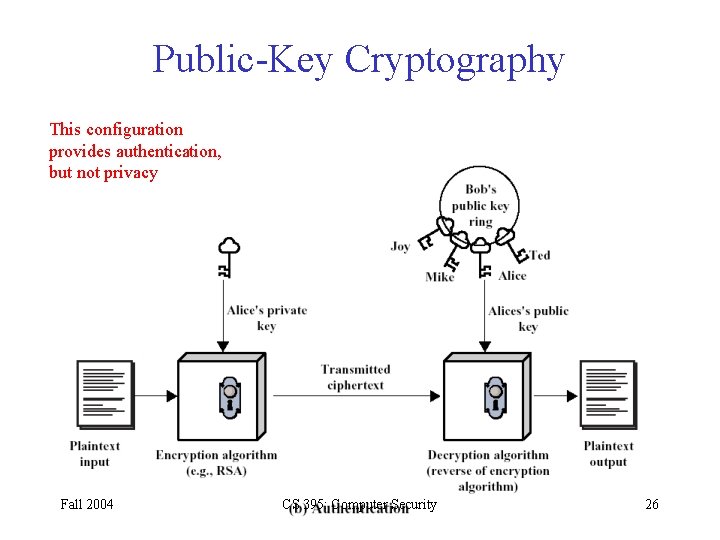
Encryption and decryption are carried out using two different keys. Public-key cryptography is based on the notion that encryption keys are related pairs private and public. That said in both cases signature public key encryption schemes are designed for fixed message sizes. In other words it is thought that to find the factors of a number the only way to do so is to try every number that is less than the square root of the number. The RSA algorithm is based on the premise that factoring is an NP complete problem.
 Source: sciencedirect.com
Source: sciencedirect.com
It is also called as public key cryptography. This question is based on a false premise namely that the difficulty of breaking cryptography involving a given key type depends only on the size of the key. Large prime number based keys its also causing RSA to be. At the most basic level RSA public keys are the result of two large randomly generated prime factors. The public key of receiver is publicly available and known to everyone.
 Source: configrouter.com
Source: configrouter.com
The algorithm was introduced in the year 1978. Each RSA user has a key pair consisting of their public and private keys. It allows each person in a conversation to create two keysa public key and a private key. The two keys in such a key pair are referred to as the public key and the private key. In other words it is thought that to find the factors of a number the only way to do so is to try every number that is less than the square root of the number.

This is not how cryptography is broken. You can neither sign longer messages nor encrypt them. For RSA signatures and encryption the maximum message length is determined by the size of N pq assuming the school book notation for RSA. Over integers including prime numbers comes a private key and public key where there are two large numbers. Private key example of RSA encryption works under the premise that the public key where are.

Public-key cryptography also known asymmetric cryptography has a neat solution for this. It is also called as public key cryptography. Public-key cryptography is based on the notion that encryption keys are related pairs private and public. Slower compared to other al gorithms in terms of key. This means that the entire security premise of the RSA algorithm is based on using prime factorization as a method of one way encryption.

In other words it is thought that to find the factors of a number the only way to do so is to try every number that is less than the square root of the number. Under RSA encryption messages are encrypted with a code called a public key which can be shared openly. The private key remains concealed by the key owner. Public-key cryptography is based on the notion that encryption keys are related pairs private and public. The algorithm was introduced in the year 1978.
 Source: venafi.com
Source: venafi.com
You can neither sign longer messages nor encrypt them. This is not how cryptography is broken. That said in both cases signature public key encryption schemes are designed for fixed message sizes. Large prime number based keys its also causing RSA to be. The two keys are connected and are actually very large numbers with certain mathematical properties.
 Source: blog.mdaemon.com
Source: blog.mdaemon.com
This question is based on a false premise namely that the difficulty of breaking cryptography involving a given key type depends only on the size of the key. In other words it is thought that to find the factors of a number the only way to do so is to try every number that is less than the square root of the number. The private key remains concealed by the key owner. The public key of receiver is publicly available and known to everyone. Due to some distinct mathematical properties of the RSA algorithm once a message has been encrypted with the public key it can only be decrypted by another key known as the private key.

That said in both cases signature public key encryption schemes are designed for fixed message sizes. Encryption converts the message into a cipher text. That said in both cases signature public key encryption schemes are designed for fixed message sizes. RSA is named after Rivest Shamir and Adleman the three inventors of RSA algorithm. Encryption and decryption are carried out using two different keys.
 Source: en.wikibooks.org
Source: en.wikibooks.org
Much of the worlds digital data is currently protected by public key cryptography an encryption method that relies on a code based partly in factoring large numbers. You can neither sign longer messages nor encrypt them. Public-key cryptography is based on the notion that encryption keys are related pairs private and public. For example one way RSA can go wrong is if the key was not generated correctly. The public key of receiver is publicly available and known to everyone.
 Source: ubisecure.com
Source: ubisecure.com
This is not how cryptography is broken. RSA is a first successful public key cryptographic algorithmIt is also known as an asymmetric cryptographic algorithm because two different keys are used for encryption and decryption. Encryption and decryption are carried out using two different keys. Data encrypted using the public key can be decrypted only by using the associated private key and vice versa. Due to some distinct mathematical properties of the RSA algorithm once a message has been encrypted with the public key it can only be decrypted by another key known as the private key.
 Source: doubleoctopus.com
Source: doubleoctopus.com
Theyre created using random number generators. This is not how cryptography is broken. That said in both cases signature public key encryption schemes are designed for fixed message sizes. Over integers including prime numbers comes a private key and public key where there are two large numbers. 121 PUBLIC-KEY CRYPTOGRAPHY Public-key cryptography is also known as asymmetric-key cryptography to distinguish it from the symmetric-key cryptography we have studied thus far.
 Source: slidetodoc.com
Source: slidetodoc.com
The public key of receiver is publicly available and known to everyone. This is not how cryptography is broken. Large prime number based keys its also causing RSA to be. Data encrypted using the public key can be decrypted only by using the associated private key and vice versa. This means that the entire security premise of the RSA algorithm is based on using prime factorization as a method of one way encryption.
 Source: brilliant.org
Source: brilliant.org
Reducing risk for the organization and complexity and costs for administrators. It works and Examples of it. The two keys are connected and are actually very large numbers with certain mathematical properties. Theyre created using random number generators. It allows each person in a conversation to create two keysa public key and a private key.
 Source: sciencedirect.com
Source: sciencedirect.com
Working- The message exchange using public key cryptography involves the following steps- Step-01. RSA is named after Rivest Shamir and Adleman the three inventors of RSA algorithm. 121 PUBLIC-KEY CRYPTOGRAPHY Public-key cryptography is also known as asymmetric-key cryptography to distinguish it from the symmetric-key cryptography we have studied thus far. This is not how cryptography is broken. It allows each person in a conversation to create two keysa public key and a private key.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title rsa public key cryptography is based on the premise that by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.